Cisco Umbrella: Web Content Filtering and Cloud Services Cybersecurity
As your organization grows, your attack surface increases when administrators add cloud resources, user devices, and more infrastructure to support business growth. With an increased attack surface, you need better security to stop common threats. Zero-trust standards also require more stringent authentication and authorization for VPN-connected devices and remote network resources. The modern network requires a modern security solution.
Cisco has several security appliances to improve your posture, and one such appliance is Cisco Umbrella. Unlike other Cisco solutions, Cisco Umbrella focuses more on the “edge,” meaning that it helps administrators monitor and authorize remote devices connecting to internal resources. Edge devices could be user-controlled devices (e.g., company issued smartphone or personal device) or remote connections from your operations team. These devices add cyber-risks to your organization, so administrators need a higher level of visibility, antimalware protection, and incident response should a user lose their laptop or smartphone. Cisco Umbrella features protect edge devices and tie into other Cisco products so that business can control access, and detect and contain threats.
What is Cisco Umbrella?
As the name suggests, Cisco Umbrella is a set of features rather than a single one. It’s a cloud-based product with web gateway, firewall, DNS-based web content filtering, data loss prevention, and CASB (Cloud Access Security Broker) features. When a user must connect to your infrastructure, Cisco Umbrella routes traffic between the device and its SIG (Secure Internet Gateway) proxy. Administrators point internal DNS to Cisco Umbrella, so traffic always hops from the SIG to the targeted system.
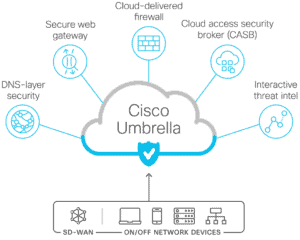
Allowing unfettered access to the internet leads to users being phished, installing malware on their devices, installing trojans or rootkits that allow remote control of the device and connecting to a command-and-control center (C2), or installing ransomware on the network. At the heart of Cisco Umbrella is the DNS-based content filtering. Between phishing, social engineering, and attacker-controlled sites hosting malware, users are your biggest threat. Many of today’s threats start with users opening a malicious website, and Cisco Umbrella stops the attack by blocking sites during DNS lookup.
For every web request, a user’s browser performs a DNS lookup to access the Fully Qualified Domain Name (FQDN) using an IP address. Instead of loading a malicious domain and leaving it to antivirus to catch issues, DNS-based web filtering blocks the browser from downloading the site and tells the user that the site is blocked. Relying on antivirus and antimalware software on the user’s device should only be used as a secondary layer to block malicious content.
DNS-based web filtering works with Cisco Umbrella’s Secure Web Gateway (SWG). SWG proxies web traffic for inspection, including inspection of HTTPS (SSL/TLS) traffic. As with any web content filtering, an effective system must adapt to changes in the cybersecurity landscape including new domains attackers register for new malware hosting. SWG adapts to changes using Cisco Talos, which is a threat intelligence system used to discover new threats. Threat intelligence is a collaborative effort between large organizations, so new threat information is shared and new threats can be identified and stopped.
Cisco’s web gateway processes 620 billion internet requests every day without causing performance degradation. The advantage to businesses is the threat intelligence automatically incorporated into the product. Zero-day threats and other new malicious domains are added to Cisco Umbrella’s database and filtered immediately. Administrators don’t need to worry about updating software with the latest threats since Cisco’s cloud infrastructure does it for them.
To add another internet safety feature, Cisco Umbrella includes a remote browser isolation (RBI) option. The RBI runs in a sandboxed environment, meaning that users with an RBI cannot install malware or execute malicious code like they would on a device with a standard browser and operating system. The RBI protects the local device and the network from being exposed to zero-day threats or unpatched vulnerabilities exploits. Think of an RBI like a virtual machine for internet browsing where users are unable to install malware on the local machine and cause the next ransomware data breach or rootkit exploit.
Included with Cisco Umbrella is another Cisco product named SecureX. SecureX ties in with Cisco’s threat intelligence and integrates Cisco products with any third-party vendors. Good security posture requires layers of defenses, and SecureX creates an ecosystem where all cybersecurity infrastructure and appliances can collaboratively detect, contain, remediate, and eradicate threats from your environment.
SecureX offers a few added benefits to your security strategies:
- Incident response: Contain threats quickly using EXtended Detection and Response (XDR) from dashboard metrics where security analysts get insights to anomalous behavior.
- Orchestration and automation: Administrators can configure playbooks for automatic containment of suspicious activity for further review. Automatic containment keeps you proactive against threats so that they cannot do further damage.
- Visibility: View the status of endpoints, edge devices, and other network resources to catch shadow IT or unauthorized connections.
- Better compliance: Incident response is often a component in compliance, and third-party risk management background checks. Should you do business involving data transfers with other organizations, their risk management background verification might ask about your incident response strategy to do business with them.
What are the Benefits of Using Cisco Umbrella?
Cisco Umbrella isn’t a single product. It’s a collection of Cisco products and services that works with third-party vendors. Umbrella is cloud-based, so deployment doesn’t require expensive hardware installed on-premises. Centralized visibility of your environment is especially useful when the environment spans several locations, resources, edge devices, and remote users.
Here are a few benefits of using Umbrella:
- Location-based browsing policies: Administrators set policies for the 80 categories Umbrella uses to organize domains. Access controls can be based on network, IP address, group, user account, or device to define permissions.
- Discover shadow IT devices: The visibility in Umbrella and SecureX help administrators identify unauthorized devices and discover malicious connections that could be used to install malware or steal data.
- Cloud-based firewalls: Umbrella offers layer 3 and layer 4 filtering based on IP address, protocol, and port number.
- Traffic inspection in transit: Network traffic –including SSL/TLS traffic– routes through the Umbrella gateway where it’s inspected for suspicious activity such as data exfiltration, command-and-control connections, malware, and ransomware.
- Threat intelligence: Integrated updates in the cloud include the latest threat intelligence findings so that your network is safeguarded from zero-day threats. The threat intelligence integrated into Umbrella lets businesses adapt to rapid changes in the cybersecurity landscape and avoid exploits.
- EXtended detection and response (XDR): Using heuristic data, Umbrella can immediately detect and contain threats. XDR ties into your orchestration and automation so that administrators can more quickly remediate threats before they can damage the environment or exfiltrate data.
Is Cisco Umbrella Right for You?
If you have Cisco products already installed and need a centralized web content security system, Umbrella is probably the best solution. It would require little overhead from your administrators, and they will find that Umbrella is a more convenient solution than working with multiple vendors.
For businesses with no web content filters and incident response, Cisco Umbrella greatly reduces risks of a compromise from various threats that come from web browsing. It blocks and contains ransomware, malware, C2 connections, and data exfiltration. Administrators can also view anomalous traffic and manually contain a threat. Automation makes containment much faster, so administrators don’t need to rely on manual detection. Playbooks and automation speed up containment and incident response, so you reduce damage in the event of a compromise or insider threat.